Blog
Articles
On our blog you will find both substantive articles and news. There will also be case studies described in detail. See the Articles category.

What is User Experience and who might find it useful to know about it
3.10.2017
If we take a very broad understanding of the term User Experience, as *the user experience encompassing all aspects of interaction with a company, its…

Errors in contracts
25.09.2017
What can be the consequences of errors in contracts? One of them is the loss of funds, as some users of the Parity wallet had a painful experience in…

Ethereum wallets
19.09.2017
We have already learned about some of the capabilities of Ethereum's *blockchain* smart contracts. In this post, I will describe in more detail one of…

What does the team know about QA?
15.09.2017
Each of us does our job to the best of our ability, regardless of which point in the software development process it involves. We try to make sure that…

Smart contracts in blockchain
7.06.2017
So far, we have stored the transaction log and balances of its users in Ethereum's private blockchain (*blockchain*) running. In the following, I will…

What is a business case
18.05.2017
All projects, or more generally --- proposals for change --- should be consistent with the business model. A project whose results are not consistent…

How to pave the way for business
12.05.2017
> "Couldn't you inform me which way I should go?
> That depends largely on where you would like to go --- replied the Cat-Beast.
> Actually, it's all…

Blockchain a way to secure data
4.05.2017
Over the past months I have discussed various cryptographic techniques. Now it's time to show their interesting applications in practice. I already revealed…

Digital signature
24.04.2017
One of the authentication mechanisms I described earlier are message authentication codes called MACs for short. It is now time to present another type…

A few words about stakeholders
6.04.2017
> "Find the right balance of competing claims of different stakeholder groups. All claims deserve attention, but some are more important than others."
>
>…

In search of lost quality
14.03.2017
"Quality is a certain degree of excellence."
With these words --- taken from Plato --- I would like to start a new series of publications introducing…
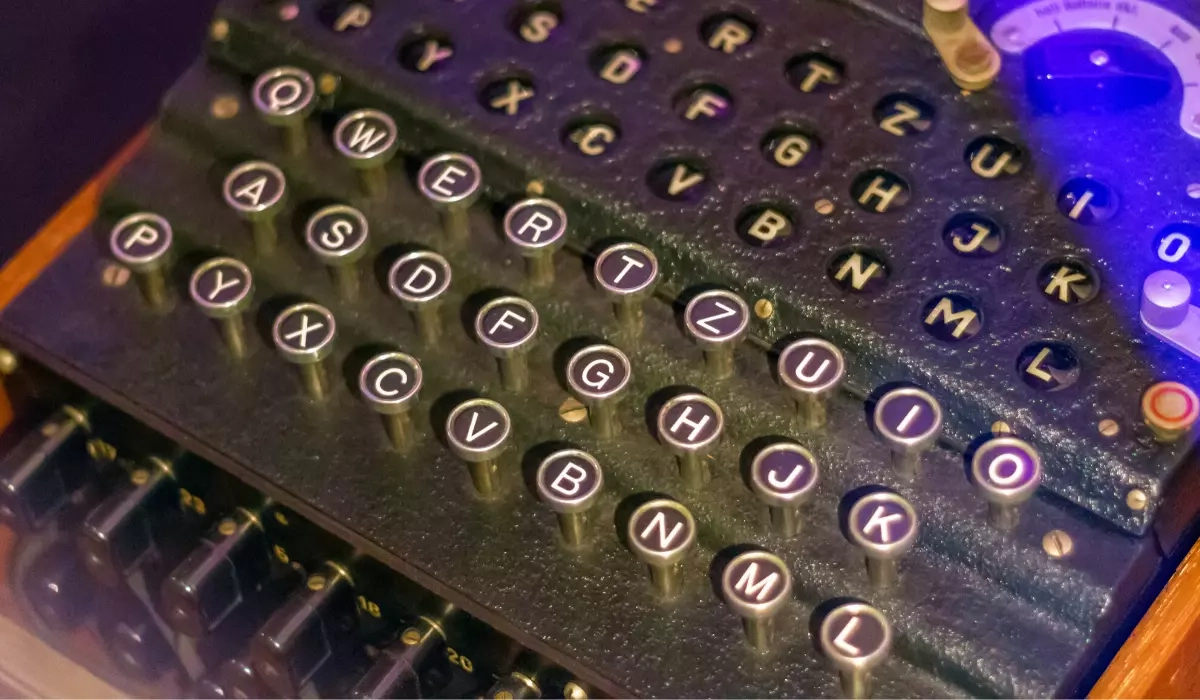
Modes of operation of block ciphers
6.03.2017
*Symmetric block ciphers* encrypt messages of a specific length that is specific to the chosen algorithm (e.g. 16 bytes for the AES algorithm, 8 bytes…