Every day, both at work and in our private lives, we enter dozens of passwords. We log in to our computer, mail, Wi-Fi, Facebook, Instagram, LinkedIn, online store, patient account and many other applications. The vast majority, if not all of these logins require us to enter a password. Are we taking proper care of the security of these passwords?
Statistics done by one security researcher show that 86% of the passwords used by users are considered very weak or on the list of passwords that have been leaked in the past, and password vulnerability bugs are on the OWASP Top 10 list, a list of the ten most common vulnerabilities of web applications.
On the subject of OWASP, or the Open Web Application Security Project, it's worth mentioning that it's a non-profit organization that aims to improve the state of application security through the creation of open access articles, methodologies, documentation, tools and technologies. One of the organization's best-known projects is actually the OWASP Top 10 list.
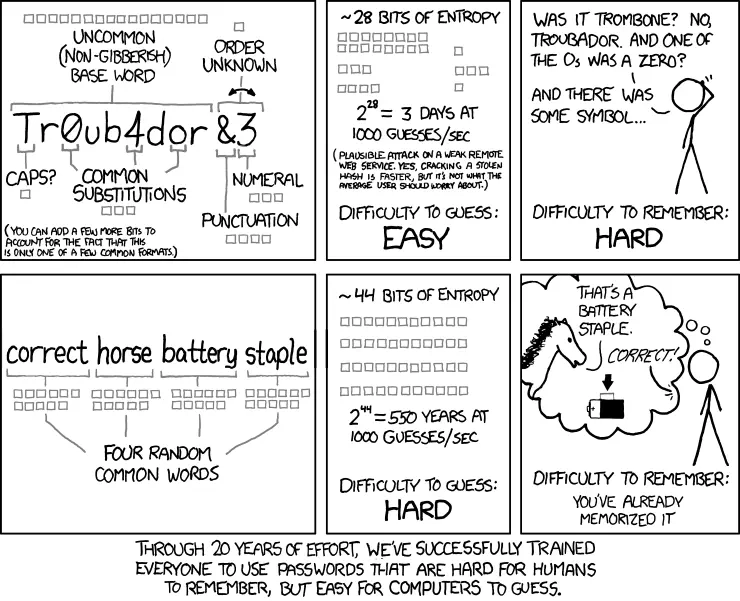
Before we get into the topic of password cracking and secure password recommendations, I refer you to a humorous graphic from the xkcd website. It illustrates the topic of password complexity and usability very well. Random passwords will not always be the best solution, and certainly it will always be a serious challenge to remember them.
Password cracking methods and features of secure passwords
Password cracking techniques can be divided into several types. Passwords can be obtained from the user through a social engineering attack, using manipulation and deception, or by guessing them based on user information and a list of commonly used passwords. Also using completely technical attacks like a brute force attack, which involves finding the password by checking all possible combinations with a script, and a dictionary attack (or a combination of the two). Not every attack can be protected against by application developers. In the case of "asking" and "guessing," one can only educate users and block the possibility of entering passwords that are too simple, but for other forms of attack, technical safeguards can be applied.
By default, a password can be called secure if its cracking time is more than 1 month (systems that do not contain important data), 1 year (most systems/applications), 10 or even 100 years (critical systems). The potential password cracking time is, of course, influenced by the amount of computing resources used, which can be estimated based on the profile of the potential attacker, for example, a government agency or a large organization could have much more computing resources than a single hacker with limited resources and means to hire a botnet (a botnet is a network consisting of computers infected with malware and controlled by the attacker). However, regardless of computing resources, longer pass words always provide a larger combination of characters, making them more difficult to crack. In addition to length, complexity is of great importance. Passwords of less than 20 characters are usually considered weak if they consist only of lowercase Latin letters. The easiest to crack and providing virtually no protection are passwords containing the most commonly used words and dictionary passwords. If you have encountered a list of the 10 most popular passwords, they are in this form. Here, depending on the data sample, such passwords appear as:
- 123456
- 123456789
- qwerty
- password
- 111111
- 12345678
- abc123
- 1234567
- password1
- 12345
However, who among us has never used a qwerty password? Why then do we use this type of password so often? The answer to this question is simple - we care about remembering the password easily, that is, usability is more important to us than security.
What passwords are not only secure but also easy to remember?
The passwords listed above, in addition to the ease of cracking, have another element in common - they are easy to remember, that is, convenient, and convenience and ease of use of the system is, after all, very important.Users choose passwords that they are able to remember. It is practically impossible to remember long random passwords to dozens of different services, in turn, forcing users to create such passwords causes them to be often forgotten or written down, usually in an easily accessible place, which significantly reduces their security. So, looking at passwords from the point of view of usability, we need passwords that are, first of all, easy to remember. What is the security of passwords consisting of words that are easy to remember? This question has already been partially answered by the linked cartoon. A password consisting of a few words of a sentence, e.g. what we are thinking about, a poem, a song (preferably not the most popular songs) separated by special characters along with numbers is virtually unbreakable using brute force and dictionary attacks. For example, the password Blue$55$Dress is much harder to crack than the randomly generated password J4fS>7, and most importantly it is much easier to remember.
Password security from the user's point of view
As conscious users, we should use complex but also easy-to-remember passwords for each service, created according to the guidelines posted above. In addition, it is very important that each password be unique and changed once in a while. Thanks to the uniqueness of the passwords, we will protect ourselves from the situation when the leak of data from one of the services causes the takeover of accounts also in other services where we use the same password. Passwords should not be written down in open text in easily accessible places (a piece of paper taped to the monitor will not be a good idea ☺) or shared. If you have trouble remembering your passwords, you can use a password manager such as KeePass. Let's return for a moment to the aforementioned statistics on the use of weak passwords. They were calculated thanks to a database of accounts and passwords leaked in data security incidents. Such a database can be found not only on hacker forums or on the darknet (the darknet is a hidden part of the Internet). We can easily search it using Have I Been Pwned. This is a service that quickly and free of charge allows us to check if our password has already leaked and we should change it immediately. We can search by our email address, and we can also set up an alert, in case our email address appears in the data from subsequent leaks. Below is a sample screen shot of the results of checking an account with the service.
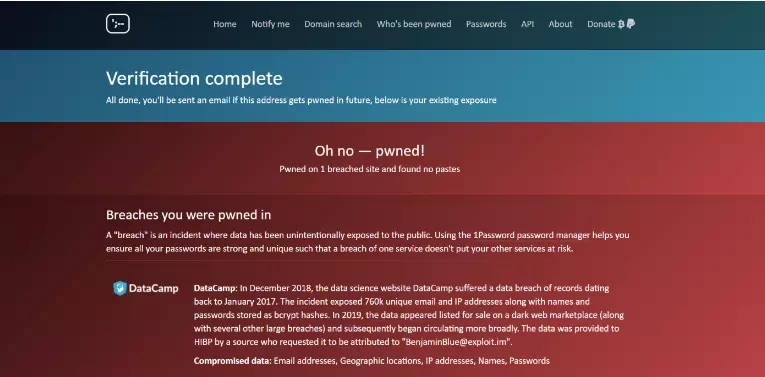
The result includes a brief information about the incident along with a list of the data that was exposed, in my example these are Email addresses, Geographic locations, IP addresses, Names, Passwords.
Password security from the point of view of application developers
In order to protect an unaware user from setting a weak password for an application, a password policy should be set appropriately for the application and the criticality of the data stored in it. OWASP recommends putting requirements on the length of the password, as well as its complexity. The application should check the minimum length of the password, preferably 10 characters, and encourage setting passwords (sentences or combinations of words) that can be much longer than typical passwords, yet easier to remember as in the earlier examples. It is also recommended to introduce protection against automated attacks in the form of adding a few seconds interval between successive logins and blocking the account or slowing down logins if several consecutive failed login attempts are detected. It is also worth enabling multi-component logins, i.e. the so-called 2FA/MFA, where, in addition to the login and password, the user must provide, for example, a code from an SMS message. You can also implement functionality to check the strength of the password and verify that the password is not on the list of the thousand weakest passwords. It should also be prevented, if possible, from listing the logins of application users. In conclusion, both when setting passwords for our private accounts in applications, and when creating or testing an application, you should not forget about password security. In applications, we should always introduce requirements for password complexity so that the user does not have the opportunity to create a very weak password. As users, we should also keep password security in mind by creating passwords that are complex but also easy to remember, preferably in the form of a few words separated by special characters.