Nowadays, a component of almost every IT system is its security architecture. It should develop from the beginning of the system's design and form an integral whole with it. Otherwise, it often turns out that it is difficult to introduce security features in an already running system without disturbing the foundations of its architecture. From my observations, the ability to understand and correctly define what we want to protect and how we want to protect it is essential so that the solution being developed doesn't turn into a *cryptographic monstrosity that no one has control over after a few weeks. The topic of this post is information security techniques shown from the inside out, that is, from the side of the basic services that accomplish this goal.
Cryptography and cryptanalysis
The science that deals with information security is cryptology. It is divided into cryptography and cryptanalysis. Cryptography is the science of constructing secure information protection systems, cryptanalysis deals with breaking them. Cryptology is handled by a cryptologist, cryptography --- a cryptographer, and cryptanalysis --- a cryptanalyst.
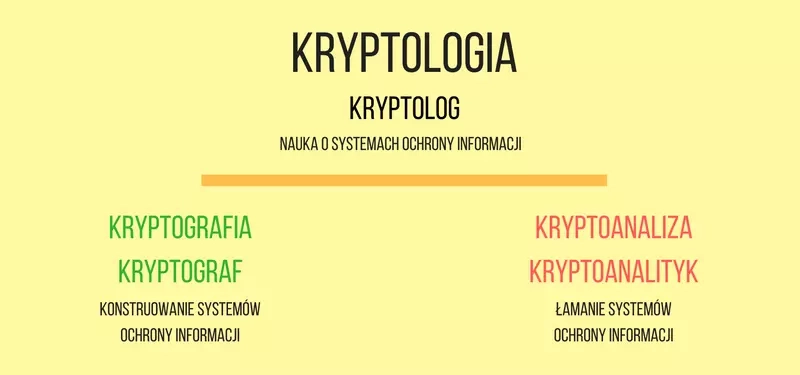
You might think that cryptanalysts are the bad guys who destroy the security features invented by cryptographers. However, it is thanks to them that we have better and better algorithms. Cryptanalysts force cryptographers to create more and more secure solutions resistant to the attacks they discover. Nowadays, one without the other doesn't exist and is equally important in the process of preparing and verifying a cryptographic algorithm. In practice, every cryptographer should also be a cryptanalyst, because in the first step he himself must conduct a cryptanalysis of the proposed algorithm.
Not only encryption
Information protection is mainly associated with the concept of confidentiality (confidentiality). It is a service aimed at securing data in such a way that it is not disclosed to unauthorized individuals. It is realized most often by means of encryption algorithms ( encryption algorithms), in which access to the secured data is possible only to entities knowing the secret key ( secret key).
Confidentiality is one of the four basic services for protecting information. The other three are integrity, authentication and non-repudiation.
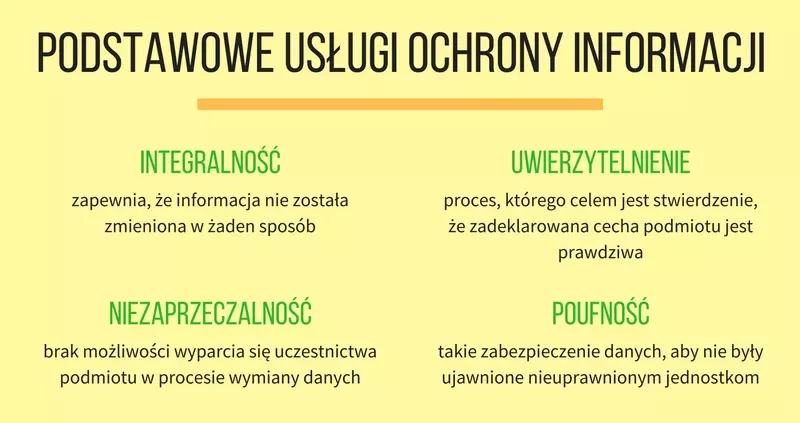
The integrity service performs the function of ensuring that the processed information has not been altered in any way. Such alteration can be accidental (transmission error) as well as intentional (alteration by an attacker). Cryptographic hash functions are used to ensure data integrity in cryptography.
Authentication ( authentication) is the process of determining that a declared characteristic of an entity is true. This sounds somewhat enigmatic. In the case of authenticating a person, it will be a process that will confirm, for example, his identity. This way we will know with whom we are communicating. Not only persons, but also systems, data sources or documents are subject to authentication. To implement the authentication service, cryptography uses passwords ( passwords), message authentication codes (MACs) and digital signatures ( digital signatures), among others.
Non-repudiation (non-repudiation) is the inability to deny an entity's participation in the data exchange process. It is a costly service to implement because it requires the collection of data for evidentiary purposes and the participation of a trusted third party. Among other things, it uses digital signatures and timestamps to prove the existence of data at a certain time. Why is a trusted third party needed when two entities are communicating? Imagine the situation of signing a contract between two parties. Each of them keeps a copy of the document with a signature. If one of the parties wants to deceive the other party simply destroys its copy and tries to prove that there was no agreement. Such an attack will fail --- the other party will pull out its copy of the document with the signature. The situation will be slightly different when both parties come to an agreement that it is better for them to liquidate the contract. Without a trusted third party keeping a copy of it, the nonrepudiation in such a system will be up for question.
The aforementioned information protection services are not completely independent of each other. The integrity service plays a special role, because without it, the other services cannot be properly implemented. For example, providing confidentiality without providing integrity is a mistake that occurs in many systems. Encryption algorithms work so that any data can be decrypted. Whether what you get makes sense is a separate question. And how to check this unequivocally when integrity is not assured?
Which security features to choose
Before we choose safeguards, we must answer the question of what kind of data and with what techniques we want to protect it. Is it necessary to ensure confidentiality? Maybe integrity and authentication are enough? Which processes should meet the condition of non-repudiation?
On the side of selecting specific algorithms, there are more general principles for choosing security. These were presented by Auguste Kerckhoffs in his article La cryptographie militaire, which appeared in 1883 in the Journal des sciences militaires. Although they relate to the service of confidentiality and even though more than 130 years have passed since their publication they are still relevant. Today, their meaning should not be read literally. If only because encryption machines have been replaced by algorithms that no longer take up half a carriage on a train.
Auguste Kerckhoffs noted that the system will be useful and virtually unbreakable if the following conditions are met:
- the construction of the machine will be explicit, only the key is secret --- translating into today's language in systems we use explicit algorithms, only the key should be secret,
- the key is easy to remember,
- cryptogram, that is, the encrypted data is easy to transmit,
- the encryption machine is handy,
- the system is easy to use.
Central to today's systems is the first principle. We do not create solutions whose security is based on hiding, making the solution secret, using an unknown algorithm ( security by obscurity). Practice shows that such systems are usually broken. We only use explicit, proven algorithms in the correct way ( security by design).
Summary
We don't always have to secure everyone and everything. Aside from the fact that it costs money, such a solution results in a system that is complicated and more difficult to use. The typical user doesn't like difficult things and his natural contrivance will be a more or less successful attempt to circumvent security. In this way, excessive demands on security can lead to a reduction in security. A paradox resulting from our human and somewhat lazy nature.
If we are already implementing security then we must do it correctly. The basic principle is to ensure integrity when implementing other services. Otherwise, they make no sense. There is nothing worse than improper use of good cryptographic algorithms. It is important to remember that a false sense of security is worse than a true understanding of danger.
There are no practically working unbreakable systems. Security has to be chosen so that it is not worthwhile for an attacker to break them. These are not easy decisions. It is sometimes said that of the three things: cheap, fast and secure, you can only choose two.
In the following posts I will discuss the mentioned information protection services in more detail, along with the modern algorithms that implement them. I will also show how to apply them in practice on the Java platform.